CyberFOX Blog
Get the latest insights and information from our cybersecurity experts. Learn more about hot industry topics including password security, identity access, and data access management. Or find answers to your cybersecurity questions in our ebooks, demos, videos, articles, and more.

What is Identity and Access Management?
Identity and access management (IAM) tools have come a long way over the past decade. Unfortunately, as security capabilities and.

5 Inexpensive Solutions that Make Huge Impacts in Your Security Stack
As cyber threats become more complex, the cost of preventing them is simultaneously rising, but the good news is that.

Everything You Should Already Know About FTC Safeguards Compliance
The deadline for complying with the updated FTC Safeguards Rule was June 9, 2023. Are you in compliance? The Safeguards.

How Two-Factor Authentication Helps You Double Down on Cybersecurity
Two-factor authentication (2FA) has been a standard security measure for over a decade. Whether logging into an online bank account,.

6 Best Practices to Keep Your IT Department Running Smoothly
Building an efficient IT department and strong tech culture is a team effort that requires the cooperation of every employee..

Why Remove Local Admin Rights?
Cybersecurity measures have improved dramatically over the past decade. As technology platforms and applications have become more sophisticated and complex,.

The UAC Conundrum: How to Manage Admin Privilege Without Frustrating Users
For many IT administrators and end-point users, administrative privilege has become a source of friction. Security best practices recommend protecting.
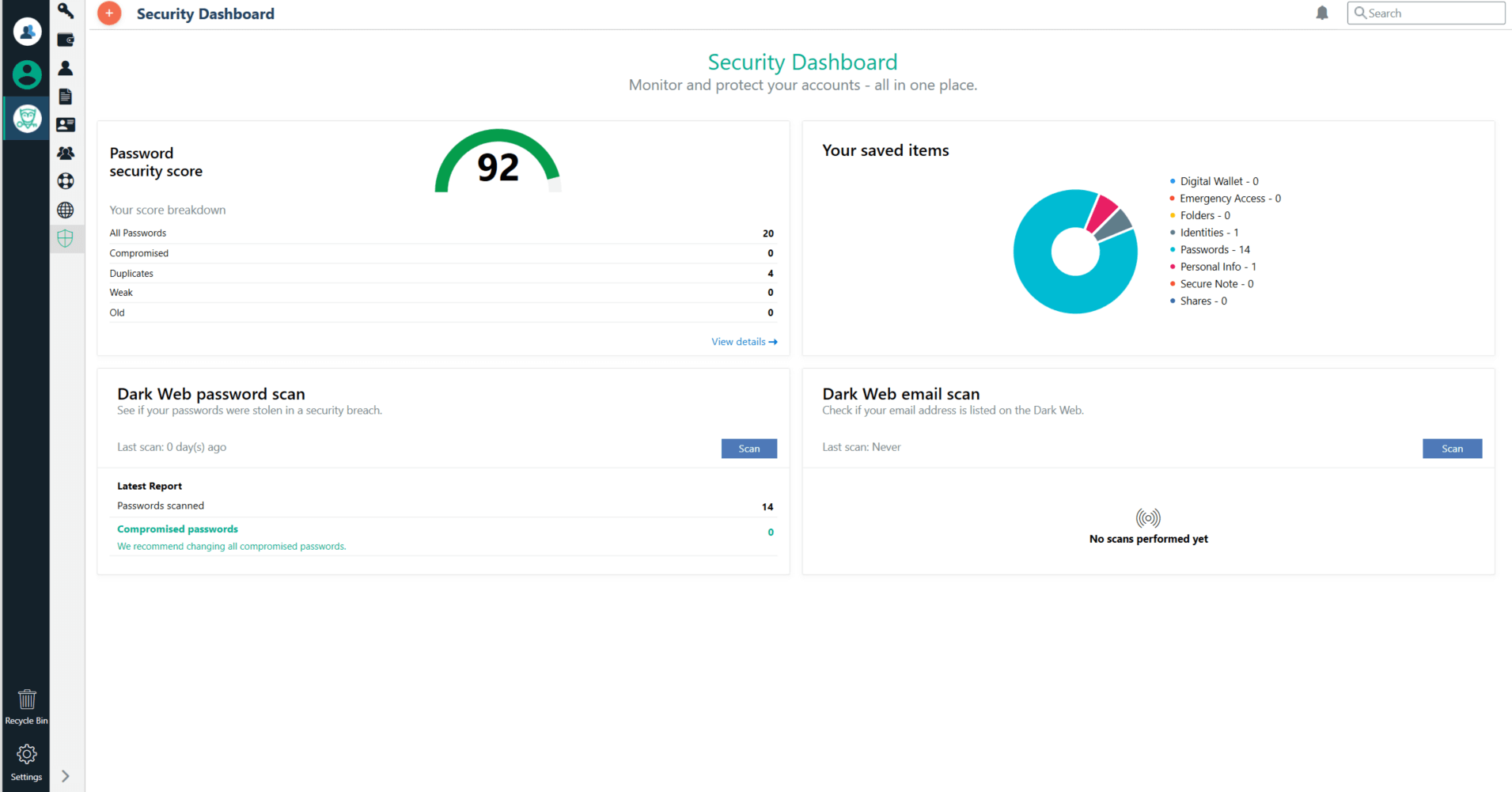
How to Neutralize Password Security Risks with Password Boss
One of the most important things you can do to reduce risk across your organization is to crack down on.

The Complete Checklist: What to do if Your Third-Party Vendor Is Breached
Outsourcing some of your business processes and services to a third-party vendor can increase efficiency, improve customer service, and help.

How to Create and Manage a Cybersecurity Culture
As cybersecurity technology continues to evolve, the good news is that new tools have delivered on their promise to shore.

The Problem with Privilege: 3 Dangers of Privileged Access
Every organization needs a secure solution that enables users to access critical information, make changes to the network, and configure.

What is My Cyber Liability?
Last year, the average cost of a data breach in the U.S. clocked in at $9.44 million, according to IBM’s.
Get the latest insights delivered to your inbox
Subscribe to identity and access management news and resources from industry experts.